
Crypto Server
Encrypt 62,300 data per second! Fast and Secure.
Over 80% of enterprise security issues arises from their own employees. Therefore, solving this issue through data encryption is the common viewpoint of all informational security personnel.
- Protect corporate confidential properties, including payroll information, potential client data, credit card data, and order data.
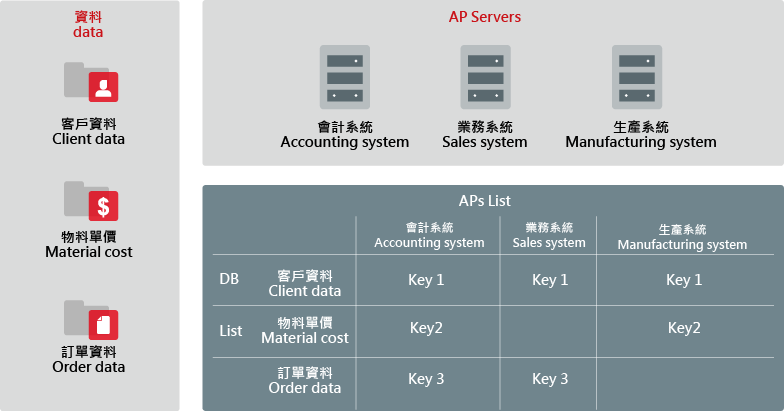
- Securely transfer data.
- Manage data of all resource allocations, monitor and manage access control and user authorization as the main focus including personal authorization management, application system authorization management and access log records.
- Utilize secure encryption methods to back up data for privacy, with the methods including symmetric encryption, asymmetric encryption, key management and efficient en/decryption.
- Personal data en/decryption.
structure
features
-
Support various database types
Including MS SQL, Oracle, MySQL, Sybase and DB2 etc.
-
Support various programming languages
Including .NET, JSP, ASP, PHP, C, Visual Basic, Delphi, Java and PowerBuilder
-
Support multiple platforms
Including Windows, Linux, Solaris, Unix and IBM AIX.
-
Key security
HSM with FIPS 140-2 Level 3 security certification, storing encryption key in HSM for prevention of stealing data and providing automatic key destroying function.
-
Flexible authorization mechanism
Establish complete application system and authorization mechanism for key; support shared use of the same key for multiple systems or use of various keys for different systems.
-
Support document and database en/decryption
Support encryption of database columns and documents.
-
Multiple en/decryption mechanisms
Support symmetric and asymmetric algorithm, as many as over 140 kinds ( 3DES, AES, ARS256, RIJNDAEL, SKIPJACK, RC6, CDMF, IDEA, BLOWFISH, TWOFISH, CAST5, CAST128, CAST256, SERPENT, RC4, SEED and CAMELLIA ).
-
De-identification rule configuration
Simple configuration of masking column and specification according personal data inventory request.
Advantages
-
![*]() A encryption, decryption, and masking platform
A encryption, decryption, and masking platform- Field encryption
- Data encryption
- File transfer needs
- Personal data masking
-
![*]() Low cost
Low cost- Flexible application and key management system
- Multi-language, cross-platform, cross-database
- Implement one platform across the whole enterprise
-
![*]() Safeguard corporate assets
Safeguard corporate assets- Ensure confidential information is never compromised
- DBA provides appropriate authorities



