
ubiquitous Identity and Access Management System
Constructing safe and convenient network environments, centralizing resource authorization and password management, integrating individual applications and security validation modes, Ares strives to provide a complete personal ARES uIAM (ubiquitous Identity and Access Management) System.
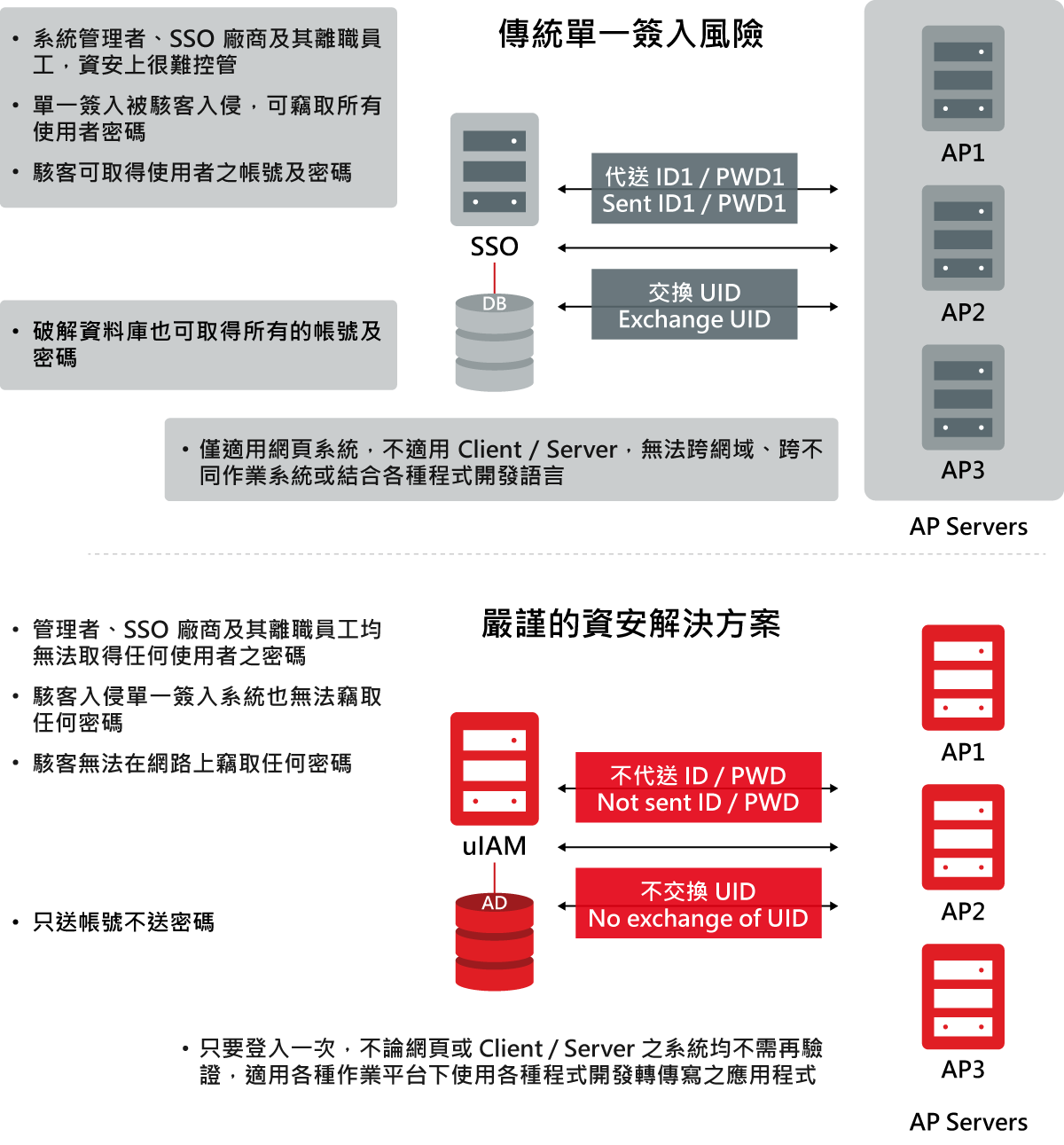
Security issues of the current Internet SSO System:
-
Hackers can easily have access to user password through the internet.
-
If the SSO system is intercepted, all accounts and passwords will be stolen.
-
If any application system is intercepted, information security will be compromised.
-
Hackers hack into database to steal all account and passwords.
-
Hackers, administrators or former employees may obtain illegal authorization and information.
-
Only applicable to a Web environment, unable to operate under cross-domain and cross-operating system environments.
ARES uIAM System solves these issues regarding Internet SSO system. Working with our uPKI digital signature validation authority will further provide a complete SSO solution for Web-based, client/server cross system platforms, and cross-programming language environments.
Structure
Differences between traditional Internet SSO and ARES uIAM system
features
Provide highly-secure authentication mechanism
- Only the account is transferred on the Internet without leaking the password to avoid interception
- Not sending any ID or password to other applications
- No ID/database account information shared between application systems
Highest level of security for application system verification
- Ensure all application systems reach same level of high security
- Unique individual validation and authorization mechanism to ensure the confidentiality of each application
- Each message is encrypted and includes information such as timestamp to prevent repeated attacks
- Mutual authentication
- Support designated, layered validation to speed up the validation process
- Support a multi-tier structure; user, Web server and DB server can locate on separate machines
- Conform to USA DoD TCSEC (Trusted Computer System Evaluation Criteria, Orange Book) specific C2-level security rules
Applicable to
-
![*]()
Various operating systems: Windows, Linux, Solaris, Unix, AIX, etc.
-
![*]()
Various development programming languages: ASP, PHP, JSP, .NET, Java, VB, VC, Delphi, Lotus, PowerBuilder, CGI, etc.
-
![*]()
Web-based and client/server structured application system for consistency of security authentication mechanism and eliminate loop holes in information security.
SSO Comparison
| ARES uIAM | Other Internet SSO | |
|---|---|---|
| Upload account and password for user authorization? | No, only uploads account | Mostly upload both account and password |
| SSO system manager has access to all user passwords? | No, uIAM does not provide any user password | Access to user account and password |
| Exchange account information and saved file with other files; Uses ID to conduct SSO? | No, we will not conduct such high-risk application | Mostly using this method because it is easy and convenient, but ignore the fact that it is rather dangerous |
| After logging in, does the system allow users to become high-authority to access other account information? | No, we assign unique authority for each user | Yes, possible conversion to high-authority user |
| If SSO is hacked, does it affect all other system processes? | No, all systems have their own unique authorization | Yes, it will affect every system |
| Support multiple development programming language? | ASP, PHP, JSP, .NET, Java, VB, VC, Delphi, Lotus, PowerBuilder, CGI, API | Only support basic development programming language |
| Support cross-domain, cross-platform authentication? | Not limited to one domain or platform, support Windows, Linux, Solaris, Unix, and AIX platform programming language application | Only support basic domain and platform |
| Support Web-based and client / server structure system? | Completely support | Client / server cannot be integrated |








